
- 27
- 1 061 110
The CISO Perspective
United States
Приєднався 7 вер 2018
The CISO Perspective was created as a free resource for the benefit of the entire cybersecurity community. Have a cybersecurity question? Send us an email for free consultation response in 4 sentences or less.
Deepfakes Using Stable Diffusion: Creating and Identifying
In this video, we dive into the world of how A.I generated fake images are created using the popular Stable Diffusion LLM. Unlike Midjourney and Open AI's DALL-E, Stable Diffusion's opensource nature has an extensive community and tools for custom training. But this hub for innovation has also sparked a wave of hyper-realistic A.I. fakes. In This video, we'll not just cover how these images are created but, more importantly, how to detect A.I. generated fake images.
Stable Diffusion Overview 0:25
Forms of A.I. Generated Fake Images 1:14
Why Stable Diffusion? 2:32
Stable Diffusion Framework for Fakes 3:16
Models and Checkpoints for Realistic Images 3:33
Training the Model (Text Embeddings and LoRa's) 4:18
Kohya_SS for Training 4:44
Using the LoRa in Stable Diffusion 5:11
User Created Model Database 5:40
How to Spot a Fake 6:12
Software Detection (AI Detectors) 9:17
Reverse Engineering a Photo 10:19
Other Fakes and Considerations 11:14
Stable Diffusion Overview 0:25
Forms of A.I. Generated Fake Images 1:14
Why Stable Diffusion? 2:32
Stable Diffusion Framework for Fakes 3:16
Models and Checkpoints for Realistic Images 3:33
Training the Model (Text Embeddings and LoRa's) 4:18
Kohya_SS for Training 4:44
Using the LoRa in Stable Diffusion 5:11
User Created Model Database 5:40
How to Spot a Fake 6:12
Software Detection (AI Detectors) 9:17
Reverse Engineering a Photo 10:19
Other Fakes and Considerations 11:14
Переглядів: 3 833
Відео
Hacking with ChatGPT: Five A.I. Based Attacks for Offensive Security
Переглядів 53 тис.Рік тому
ChatGPT may represent one of the biggest disruptions in modern history with it's powerful A.I based chatbot. But within weeks of ChatGPT's release, security researchers discovered several cases of people using ChatGPT for everything from malware development to exploit coding. In this video, take a look at the five ways attackers are utilizing ChatGPT for wrong doing. 0:14 Intro to ChatGPT / Nat...
What is Security Service Edge (SSE)? SASE vs SSE vs VPN
Переглядів 50 тис.2 роки тому
In this video, we compare traditional VPN vs SASE and SSE (Security Service Edge). SSE and SASE are categories of technology that provide Cloud-delivered security services. We’ll review the components that make up SASE and SSE, and look at how these two similar services compare. The Problem with VPNs 0:01 Secure Access Service Edge (SASE) Overview 1:28 SASE Components 2:10 SASE Integration 3:08...
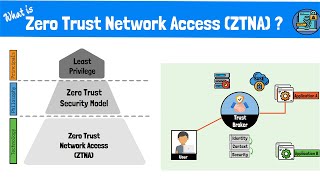
What is Zero Trust Network Access (ZTNA)? The Zero Trust Model, Framework and Technologies Explained
Переглядів 105 тис.2 роки тому
Zero Trust Network Access (ZTNA) is a technology that is quickly replacing VPN’s as a more secure and scalable way to provide remote connectivity. Unlike VPNs, Zero Trust provides a scalable way to provide secure connectivity without the need of centralized equipment. In this video we take a deep dive on Zero Trust Network Access (ZTNA) and walk through the models, principles and architectures ...
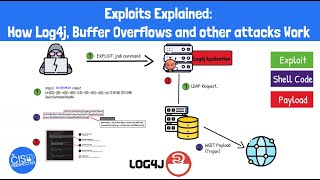
Exploits Explained: How Log4j, Buffer Overflows and Other Exploits Work
Переглядів 14 тис.2 роки тому
Exploits represent any piece of code, data or sequence of commands that targets a vulnerable application for the purpose of gaining unauthorized access. Log4j is one of the most popular recent exploits that is widely considered to be the most dangerous exploit of our time. In this video, we will break down the anatomy of an exploit, and how each part of the malicious code comes together to targ...
Hacking Two Factor Authentication: Four Methods for Bypassing 2FA and MFA
Переглядів 64 тис.2 роки тому
Bypassing multi-factor authentication was once considered more of a proof of concept then an actual threat. In this video, we will review four common techniques an attacker will utilize to hack multi-factor and two-factor authentication. We’ll review Evilgenix2, which is a popular framework for stealing authentication cookies, and other methods that an attacker can utilize to bypass the authent...
What is AIOps and MLOps? Artificial Intelligence for IT Operations Explained
Переглядів 16 тис.2 роки тому
AIOps (also known as MLOps) is a combination of big data with machine learning to enhance IT operations. Using artificial intelligence, the system can find and predict network issues in real time. With Gartner predicting an increase of 700% over the next three years, this technology is only just beginning. In this video, we'll review what AIOps is, uses cases, and the five Gartner components th...
T-Mobile Data Breach: Timeline, Analysis and Lessons Learned
Переглядів 8 тис.2 роки тому
The most recent T-Mobile hack is one of the largest data breaches in US history. 50 million current and former T-Mobile customer records containing social security numbers, driver's licenses, addresses, and phone numbers have made their way to dark web forums. In this video, we'll review the timeline of events, as well as what T-Mobile could have done differently to stop this attack from ever o...
What is XDR vs EDR vs MDR? Breaking down Extended Detection and Response
Переглядів 183 тис.2 роки тому
Extended Detection and Response (XDR) is a cybersecurity tool that integrates with multiple products to detect and respond to threats. While EDR (Endpoint Detection and Response) focuses on the endpoint, XDR uses A.I. to ingests information from multiple sources and detect patterns across different device types. In this video, we'll discuss what XDR is and how it compares to EDR and MDR (Manage...
What is Machine Learning ? A.I., Models, Algorithm and Learning Explained
Переглядів 22 тис.3 роки тому
In this video, we go over what Machine Learning is and how it works within the Artificial Intelligence framework. We’ll review the Machine Learning model, learning methods and the algorithms used for different use cases. A.I. vs Machine Learning vs Deep Networks 0:42 Machine Learning Overview 1:18 Machine Learning Model 1:45 Supervised Learning 2:15 Unsupervised Learning 2:40 Semi-Supervised Le...
Cyber security Kill Chain: Active Reconnaissance Overview, Methodology and Tools
Переглядів 8 тис.3 роки тому
Reconnaissance is the first in the cyber security kill chain and it involved both passive and active techniques to obtain information about a target. Once an attacker has used Opensource Intelligence (OSINT) for passive reconnaissance, they generally move on to active techniques of information gathering that involve direct interaction with a target. In this video, we'll discuss active the activ...
What is Open Source Intelligence (OSINT)? The OSINT Tools, Techniques and Framework Explained
Переглядів 30 тис.3 роки тому
Reconnaissance is the first step of the cybersecurity kill chain and the foundation to a successful attack. Open-source Intelligence (OSINT) is the practice of collecting publicly available information about a target. In this video, we'll cover what OSINT is, the framework and methodology for an OSINT investigation and some of the top tools in OSINT data investigation. What is OSINT (Open-sourc...
What is Secure Access Service Edge (SASE) ?
Переглядів 118 тис.3 роки тому
Secure Access Service Edge (SASE) is a term coined by Gartner that combines some of today's most popular technologies into a single solution. In this video we'll cover what SASE Core, Recommended and Optional levels include and how the various technologies work together. SASE Core, Recommended and Optional 0:47 Why SASE? 1:32 Zero Trust Network Access 2:33 SASE Endpoint (Off-net vs on-net) 3:20...
How to Use Canary Tokens for Threat Hunting
Переглядів 22 тис.3 роки тому
How to Use Canary Tokens for Threat Hunting
NextGen Firewall & IPS Evasion: 5 Defensive Techniques
Переглядів 7 тис.4 роки тому
NextGen Firewall & IPS Evasion: 5 Defensive Techniques
Securing Your VPN: Six Considerations
Переглядів 8 тис.4 роки тому
Securing Your VPN: Six Considerations
The Iran Cyber Threat: What You Need To Know
Переглядів 3,6 тис.4 роки тому
The Iran Cyber Threat: What You Need To Know
VNF: Five Considerations in Virtualizing Your Perimeter
Переглядів 2,4 тис.4 роки тому
VNF: Five Considerations in Virtualizing Your Perimeter
Securing Your AWS Virtual Private Cloud
Переглядів 9 тис.5 років тому
Securing Your AWS Virtual Private Cloud
Accomplishing Zero Trust Security Using SDP
Переглядів 35 тис.5 років тому
Accomplishing Zero Trust Security Using SDP
Breaking The Kill Chain: A Defensive Approach
Переглядів 155 тис.5 років тому
Breaking The Kill Chain: A Defensive Approach
5 Terrifying Cyber-Security Trends for 2019
Переглядів 26 тис.5 років тому
5 Terrifying Cyber-Security Trends for 2019
5 Considerations: Sizing Your Next-Gen Firewall (NGFW)
Переглядів 52 тис.5 років тому
5 Considerations: Sizing Your Next-Gen Firewall (NGFW)







Great channel and awesome presentation of acronyms that usually get misunderstood and confused, Keep up the good work!
Thank you very much for this video.
Very informative, thanks Andy.
I know a genius when I hear one. Super informative and very well described. Subscribed
wow! very informative. thank you so much.
Great video - Complete, concise and direct.
Great explanation. Thank you Andy
If I use my accounts what next do I do to the last option
Do you own research first. This video is a good overview, but Zscaler has a far superior offering as compared to Netskope. For example, Zscaler has had Velo Cloud SD WAN support for quite some time.
I love you!!
@great job, love your job. pls keep it up and do more of new technologies update! 👏
simple and straight to point, its great
Is a great video but need to have better sound.
E xcellent, thank you
great video! Is there a video that shows exactly what every day people should be doing to best secure accounts? Like how to use the google authenticator? etc? recommendations would be awesome. Thanks!
🎉❤ 501c3 Private Attorney Generals Associate Network 4th district OREGON Primary electronic electorial University . ❌
Perfect video about the subject ..
Great content . Subscribed. Please continue
Well done and thanks for your time.
Very Good Overview! Thank you!
Did not understand a word😢
thank you
Perfectly explained. Thank You. 5 stars.
Great presentation of technology.
I usually do not comment on videos. But this is the best video UA-cam has. 1000000%.
Most security products and strategies are not new or advanced. This includes the ‘Zero Trust’ strategy, regardless of how frequently vendors mention it. Authentication being used behind the firewall and on the internal devices of a network has been used for decades.
This is a great summary video. Thank you!
after watching this video if you don't understand the kill chain steps you never will, great work and thank you for this video
GREAT VIDEO! helped me a lot, question when you say NAC or network access control stops at layer 2, what do you mean by that? same subnet?
Amazing!
thanks for this excellent video 👍🏻😀
great explanation ... thanks much
Excellent. Simple, yet informative. Good visuals, too. Just subscribed.
You talked about hackers in the last video, How do we prevent being hacked? or How do we find out if we are already hacked? Thats actually really important stuff to know!
I hope you will make that video about KSS also. Thanks for this great lesson!
Would love to see a video on SS. Just getting started.
This is the BEST video on Stable Diffusion i have ever seen. Thank you!!
Welcome back 😇
Thank you! Alot of life changes but trying to put out more content this year. Thanks for watching!
I must say, you do amazing job in explanation, I love your way of presentation, very clean, easy to understand.. keep up the awesome work. May god bless you to achieve everything tha t you wish for yourself..
Well-illustrated and explained. Thanks a lot!.
By far the best video illustrating the use of the MIGRE ATT&CK. I really enjoyed your delivery and detail explanation; simple, no heavy technical jorgon, just right. Awesome work!! 🎉
The videos are quite informative, but they sound like I'm listening to a vendor's pitch.
Another example of no one in “zero trust “ can even agree on how many pillars there are. 3 here. 5-7 with the gov
Clear explanation and best video on Zero Trust
💥 *Promo SM*
Yoda was here. Yoda says: "Best video I've seen, on Zero Trust this is. Strong with the Force, this CISO is."
❤ very good video. Just correct the name of provider CloudfLare
Simple. Helped me find my answers in one-step. Thank you.
I broke my phone with the authenticator app and now I've tried everything, and I can't come in my Instagram